Lichen, Extraterrestrials, Diodes #2
2020-05-16, post № 229
art, #LED
2020-05-16, post № 229
art, #LED
2020-04-22, post № 228
Java, programming, #anti-pattern, #anti-patternism
Whilst pondering the lost control one has over pastebin posts as a guest; the inability to remove a text one has published themselves and the entailed virtually temporally unbounded availability to anyone of this text, I decided to look at pastebin’s “archive” site — a chronologically sorted collection of the most recent public pastebin posts.
One interesting post was titled Filter — Stringrid — Delphi and appears to be a Delphi program with German comments accomplishing some two-dimensional array manipulation task.
However, when looking further down the archive, a post published around two minutes earlier caught my attention — exmp1 [1]. This innocuously titled Java source file upon closer contains inspection an impressive 𝟥𝟦𝟫 lines of code. Now, source files of such a line count are not unreasonable (especially when writing Java), however it is not the typical size of an example — as this paste’s title suggests.
Thus, I decided to read it to know what it is meant to accomplish and how it is written — the source’s line count is highly misleading regarding its functionality.
2020-04-18, post № 227
programming, #customization, #prompt, #zsh
I have been using zsh for a while now, and whilst I like its minimalistic approach, I felt that my prompt lacked a certain graphical oomph.
Thus, I built what most graphical environments hide away at the screen’s corner directly into the prompt — a clock. Paired with a time-sensitive rainbow color scheme, I find the result quite visually pleasing.
If you want to try out my prompt, the following installer automatically downloads jprompt.c, compiles it and asks if .zshrc should be set up to load my prompt.
Since my blog has moved, the following script might not work properly.
% curl --silent https://www.jfrech.com/jblog/post227/install.zsh | zsh
2020-03-21, post № 226
programming, Zpr'(h, #esolang
I have designed and implemented a new esoteric programming language called Zpr’(h. It is a language built upon iterated symbolic pattern matching, requiring the user to define their own semantics and interpreting them as computations.
Whilst developing Zpr’(h, I implemented a rudimentary standard library, defining semantics for natural numbers, mappings, lists and logic. Furthermore, I used these semantics to define a lazy computation of all prime numbers — albeit executing at a rather slow pace.
Having finalized the language’s specifications I began investigating its computational bounds. After all, testing primality is a primitive recursive relation. Thus, it a priori is not even clear if Zpr’(h is Turing complete — a useful feature for a programming language to have.
Pondering this question, I thought about how to show that Zpr’(h is indeed Turing complete — driven by hope that I have not created a primitively weak language. I briefly thought about implementing a Turing machine but quickly opted to implement a brainfuck interpreter — equivalent, since both can simulate each other.
After having written said brainfuck interpreter (zprh_brainfuck.zpr), I proceeded to test it only to realize that using byte-based pattern matching to implement a brainfuck interpreter in a functional manner does not lead to the most efficient implementation. Interpreting the brainfuck program ++[->+++<]>. — that is, multiplying two by three — takes a respectable twenty seconds at 𝟦.𝟢𝟢 GHz. Yet more excruciatingly, adhering to commutativity and interpreting +++[->++<]>. yields the same correct numerical result, although at a steep slowdown to over three minutes.
Time constraints are not the only factor — since the current Zpr’(h implementation does not alias any byte sequences if long byte sequences are duplicated, the memory footprint rises to the unmanageable, easily blowing the 𝟣 GiB provided by default. Increasing the available memory most likely not make much of a difference given the aforementioned exponential behavior.
Thus, testing larger brainfuck programs appears not to be feasible due to computational resource limitations. Nevertheless, I am now fairly certain of Zpr’(h being Turing complete, even though my brainfuck implementation may not be correct.
To input brainfuck source code into the above interpreter, I used this translator.
Not being satisfied with a nigh untestable brainfuck implementation, I attempted to fulfil another classical interpretation of computability; recursive functions. As seen above, primitive recursive functions can already be modelled, leaving only the existence of µ-recursion open; a one-liner using the standard library:
(µ .p) |> (head (filter p |N0))
In conclusio, I am convinced that Zpr’(h is Turing complete, if not very efficient — a common fate of esoteric programming languages.
As a side note, implementing the Ackermann-Peter function is fairly intuitive: zprh_ackermann-peter.zpr
I have also golfed in Zpr’(h; it is not the most terse language out there.
2020-02-22, post № 225
C, games, programming, #board game, #Contact, #stochastic analysis
Contact is a board game designed by Ken Garland in which players draw square tiles containing colored connections from a pile, attempting to form matches. Whilst the game is enjoyable to play — allowing the odd trading of cards in unfortunate circumstances — it seldom leads to a complete configuration, meaning a valid contacting arrangement using all available cards.
With the power of stochastically driven brute-force, however, finding such complete configurations turns out to be feasible — at least when playing with the 𝟣𝟦𝟢 cards my Contact version contains. Not surprisingly, many solutions are of rather linear nature since the game only contains two branching cards, i. e. cards where three sides boast connections.
Thus, the search is further narrowed in by demanding a maximum dimension, that is the final configuration has to lie in a card rectangle of a given area. From my testing, a maximum dimension of 𝟧𝟢𝟢 is moderately quickly computed (~ 𝟥𝟢 sec @ 4.00 GHz), whilst lower maximum dimensions appear to be less likely.
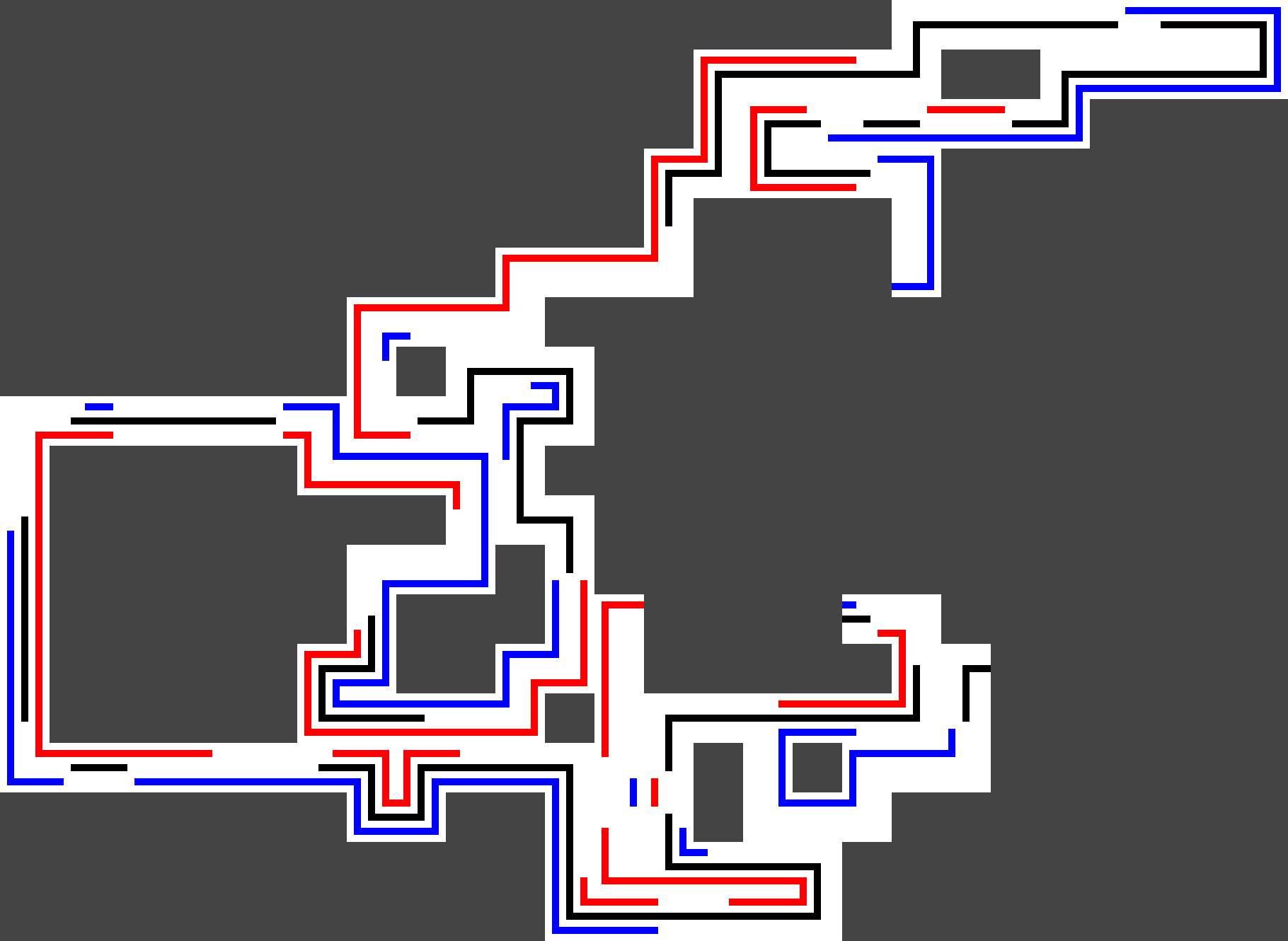
From an implementation point of view, a generalized Contact card (defined as four sides, each with three nodes being blank or colored one of three colors) snuggly fits into 𝟤𝟦 bits, allowing for card rotation, reflection and match determination being implemented through integer bit fiddling.
The stochastic process is driven by an (ideally assumed) uniformly distributed random number generator, being recursively applied until all cards are consumed. Finally, an image is created as a portable pixmap .ppm and resized to a .png using ImageMagick.
Source code: complete-contact-configurations.c
2020-01-25, post № 224
C, Haskell, mathematics, programming, #algorithms, #false implementation, #probability theory
A shuffle of a finite sequence of length 𝑛 of distinguishable elements refers to an algorithmic process which — modulo pseudo-randomness — can be modeled as a random variable uniformly distributed on the permutations .
However, most pseudo-random entropy sources provide only a pseudo-uniformly distributed realization of , leading to the necessity of finding an algorithmic transformation process if one wishes to achieve a shuffle.
In the following, I will assume that a transforming process to a family of independent and uniformly on distributed random variables is already present for any
.
One naive and seemingly correct (it is not) approach is to traverse the given sequence, uniformly swapping the current entry with another one, i. e.
void falseShuffle(uint64_t *arr, size_t len) {
for (size_t j = 0; j < len; j++)
swap(arr, j, unif(len)); }as an exemplary C implementation where is independent and uniformly distributed on
.
falseShuffle was indeed non-trivially distributed uniformly. Without loss of generality, all involved probability spaces were finite. Then there had to exist a surjection from this algorithm’s entropic state to One possible reason for the surprising nature of this non-uniformity is the striking source code resemblance to a correct implementation, i. e.
void shuffle(uint64_t *arr, size_t len) {
for (size_t j = 0; j < len; j++)
swap(arr, j, j + unif(len - j)); }as an exemplary C implementation which can be inductively shown to resemble the same structure as , in each step sprinkling in some uniform randomness and thus being itself uniformly distributed.
To see just how non-uniform falseShuffle is, I have calculated its discrete density for 𝑛 = 𝟦:
[ | ] [ | ||| ] [ | ||| ] [ | ||| ] [ || ||||||| || ] [||||| |||||||| ||| ||] [|||||||||||||||||| || ||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] [||||||||||||||||||||||||] n = 4
If it was uniformly distributed, the discrete density would look like a rectangle; [||||| ... |||||]. Further plots for 𝟢 ≤ 𝑛 ≤ 𝟨 are shown in non-uniform-shuffling.txt.
Source code for the analysis and plotting: non-uniform-shuffling.hs. Empirical evidence of non-uniformity: non-uniform-shuffling.c.
2019-12-28, post № 223
brainfuck, mathematics, programming, #recursive, #Thue-Morse sequence
[-]<<<[-]<<<[-]<<<[-]<<<[-]<<<[-]>>>>>>>>>>>>>>>>>[-]++++++++++++++++++++++++++++++++++++++++++++++++.[-]<[-]>>[-]<[-<+>>+<]>[-<+>]<<<<<[-]>>>[<<<+>>>-]<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<[<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<]<[-]<[>+<-]>>+<<<<<<<<<[-][-]>>>>>>>>>[>>>>>>>>>]>>[-]+[>[-]+[<<[-]<<<<<<<<<<[<<<<<<<<<]>>>>>>>>>[-]>>>>>>>[-]<<<<<<<<[>>>>>>>>+<<<<<<<<-]>>>>>>>>>>[>>>>>>>[-]<<<<<<<<<[>>>>>>>>>+<<<<<<<<<-]>>>>>>>>>>>]<<[>>>+<<<-]>>>>>>[-]<<<[->>>+<<<][-]>>>>[-]<[-<<<+>>>>+<]>[-<+>]<<<<<<<<<<[-]>>>>>>[<<<<<<+>>>>>>-]<<<<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<[<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<]<[-]<[>+<-]>>+<<<<<<<<<[-][-]>>>>>>>>>[>>>>>>>>>]>>>>>>>>[-]+<[->[-]<]>[-<+>]<<<<[-]>>>>[-]<[-<<<+>>>>+<]>[-<+>]<<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<[<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<]<[-]<[>+<-]>>+<<<<<<<<<[-][-]>>>>>>>>>[>>>>>>>>>]>>>>>>>[-]<<<<<<<<<<<<[-]>>[<<+>>>>>>>>>>>>+<<<<<<<<<<-]<<[>>+<<-]>>>>>>>>>>>>>>[-]<<[->>+<<]>>][-]+[<<[-]<<<<<<<<<<<<<[<<<<<<<<<]>>>>>>>>>[-]>>>>>>>[-]<<<<<<<<[>>>>>>>>+<<<<<<<<-]>>>>>>>>>>[>>>>>>>[-]<<<<<<<<<[>>>>>>>>>+<<<<<<<<<-]>>>>>>>>>>>]<<[>>>>>>+<<<<<<-]>>>>>>>>>[-]<<<[->>>+<<<][-]>>>>[-]<[-<<<+>>>>+<]>[-<+>]<<<<<<<[-]>>>[<<<+>>>-]<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<[<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<]<[-]<[>+<-]>>+<<<<<<<<<[-][-]>>>>>>>>>[>>>>>>>>>]>[-]<<<<<<<<<<<<<<<[-]>>[<<+>>>>>>>>>>>>>>>+<<<<<<<<<<<<<-]<<[>>+<<-]>>>>>>>>>>>>>>>>>[-]<<[->>+<<]>>][-]+[<<[-]<<<<<<<<<<<<<<<<[<<<<<<<<<]>>>>>>>>>[-]>>>>>>>[-]<<<<<<<<[>>>>>>>>+<<<<<<<<-]>>>>>>>>>>[>>>>>>>[-]<<<<<<<<<[>>>>>>>>>+<<<<<<<<<-]>>>>>>>>>>>]<<[>>>>>>>>>+<<<<<<<<<-]>>>>>>>>>>>>[-]<<<[->>>+<<<]>>>>[-]++++++++++++++++++++++++++++++++++++++++++++++++>[-]<<[->+>+<<]>>[-<<+>>]<.<<<<[-]>>>>[-]<[-<<<+>>>>+<]>[-<+>]<<<<<<<[-]>>>[<<<+>>>-]<<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<[<<<<<<<<<<<[-]>>>>>>>>>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<]<[-]<[>+<-]>>+<<<<<<<<<[-][-]>>>>>>>>>[>>>>>>>>>]>[-]<<<<<<<<<<<<<<<<<<[-]>>[<<+>>>>>>>>>>>>>>>>>>+<<<<<<<<<<<<<<<<-]<<[>>+<<-]>>>>>>>>>>>>>>>>>>>>[-]<<[->>+<<]>>]<]
2019-11-30, post № 222
mathematics, #F2, #OEIS
For any natural number 𝑛, let denote the set of all operations on a set of that order. An operation ★ shall be called commutative iff
and be called associative iff
holds.
With the above defined, one may study . For 𝑛 = 𝟤, this set is nonempty for the first time, containing a manageable two elements, by name
However, based on the superexponential nature of , the sequence
likely also grows rather quickly, OEIS only listing four members;
Based on this limited numerical evidence, I would suspect the commutative yet non-associative operations to be rather sparse, i. e.
Analysis source: factoids-1_operations.hs
(Non-)commutative and (non-)associative operations have also been studied nearly twenty years ago by Christian van den Bosch, author of OEIS sequence A079195. Unfortunately, their site appears to be down, which is where they hosted closed binary operations on small sets (resource found on web.archive.org).
Let 𝜀 > 𝟢 be an arbitrary distance, define . Then
has two local maxima at - 𝟣 and 𝟣, whose vertical distance is 𝜀.
It holds that .